The purpose of this article is to show you how to tell if someone is impersonating your email address and what you can do after you find out that they are. The reason you need this skill is that you may receive return emails that look like they originated from you but which bounced . Most commonly, these emails will have been sent to third party addresses you are unfamiliar with and did not send anything to.
In running this website, we have frequently been the target of several unknown persons who were impersonating (also called "spoofing") our source email address. Most often, this happens during times that there is a widespread virus infestation, and the symptom is that our email inbox gets flooded by emails that look like they were returned but which we never sent. Below is an example returned email message sent by someone who was spoofing our email address, which we have color-coded to show how this works:
This message was created automatically by mail delivery software.
Message violates a policy rule set up by the domain administrator
Delivery failed for the following recipients(s):
ewhr@edwards.com
----- Original Message Header -----
Received: by mail6-kan (MessageSwitch) id 1062107549539335_11622; Thu, 28 Aug 2003 21:52:29 +0000 (UCT)
Received: from LIZAVETA (h-66-134-52-82.LSANCA54.covad.net [66.134.52.82])
by mail6-kan.bigfish.com (Postfix) with ESMTP id C9257174762
for <ewhr@edwards.com>; Thu, 28 Aug 2003 21:52:03 +0000 (UCT)
From: <johnhamilton@aol.com>
To: <ewhr@edwards.com>
Subject: Re: Wicked screensaver
Date: Thu, 28 Aug 2003 14:50:29 --0700
X-MailScanner: Found to be clean
Importance: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MSMail-Priority: Normal
X-Priority: 3 (Normal)
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="_NextPart_000_00467D97"
Message-Id: <20030828215203.C9257174762@mail6-kan.bigfish.com>
The boldfaced blue lines indicate information about the environment that the email was sent from. The red boldfaced lines above indicate the email program that was used to send the message. This information must match our information precisely or it is bogus. The route of delivery is in reverse order with the most recent on the top of the message. Therefore, the "mail6-kan.bigfish.com" server was the last mail server to receive this message before it bounced, and was returned. The blue area above says the IP address that the mail was sent directly from was "66.134.52.82". This is NOT our IP address. The User Agent the email was sent from (which was "66.134.52.82") was the wrong IP address, so it can't be ours.
The first step in knowing that the above information about you is incorrect is to send yourself an Email. When you get it back, examine the header information. In Microsoft Outlook, you can do this from the View->Options menu. The following dialog box will pop up showing you the message header at the bottom. The content of the header tells you your specific information.
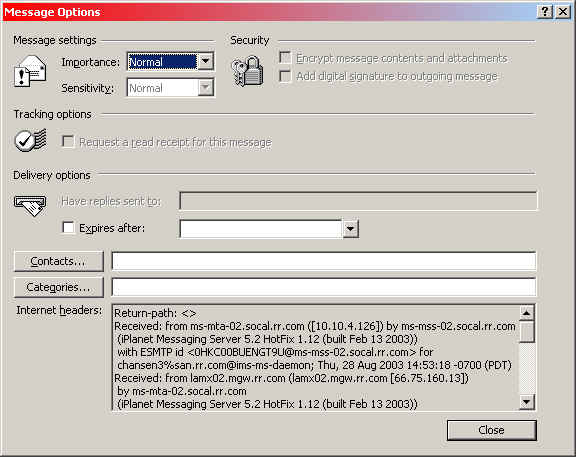
The bottom area that says "Internet headers" is the area you want to examine. We cutoff the bottom part of the header so you couldn't see our specific info. Below is the header that appeared in an email that we sent ourself that has been modified to protect our privacy, so you can see what is looks like without finding out how to spoof us. The header below is something that a user can't modify or spoof, so it can't be fabricated or rendered incorrect in order to fool you, because it is generated by the computer and the email program you are using as the message is sent out:
Return-path: <JohnDoe@san.rr.com>
Received: from ms-mta-01.socal.rr.com ([10.10.4.125]) by ms-mss-02.socal.rr.com
(iPlanet Messaging Server 5.2 HotFix 1.12 (built Feb 13 2003))
with ESMTP id <0HKC00BHVNLQ9U@ms-mss-02.socal.rr.com> for
chansen3%san.rr.com@ims-ms-daemon; Thu, 28 Aug 2003 14:56:14 -0700 (PDT)
Received: from orngca-mls02.socal.rr.com
(orngca-mls02.socal.rr.com [66.75.160.17]) by ms-mta-01.socal.rr.com
(iPlanet Messaging Server 5.2 HotFix 1.12 (built Feb 13 2003))
with ESMTP id <0HKC00DGMMLQ5N@ms-mta-01.socal.rr.com> for chansen3@san.rr.com
(ORCPT johnhamilton@aol.com); Thu, 28 Aug 2003 14:34:39 -0700 (PDT)
Received: from UserMachineName (99-99-99-99.aol.com [99.99.99.99])
by orngca-mls02.socal.rr.com (8.11.4/8.11.3) with SMTP id h7SLq2b13382 for
<johnhamilton@aol.com>; Thu, 28 Aug 2003 14:52:02 -0700 (PDT)
Date: Thu, 28 Aug 2003 15:02:57 -0700
From: John Hamilton <johnhamilton@aolcom>
Subject: Teset
To: John Hamilton <johnhamilton@aol.com>
Message-id: <NABBJOABNBOLLEFJJPLOGEFFDGAA.chansen3@san.rr.com>
MIME-version: 1.0
X-MIMEOLE: Produced By Microsoft MimeOLE V6.00.2800.1165
X-Mailer: Microsoft Outlook IMO, Build 9.0.2416 (9.0.2911.0)
Content-type: text/plain; charset=iso-8859-1
Content-transfer-encoding: 7bit
Importance: Normal
X-Priority: 3 (Normal)
X-MSMail-priority: Normal
Original-recipient: rfc822;JohnDoe@san.rr.com
Notice that the IP address of "99.99.99.99" above does not match the source IP of the person above who was impersonating our email address. That persons address was "66.134.52.82". Also notice that an email send program was used by the imposter that did not match the one we use. The header above shows in red that we use "Microsoft Outlook IMO" while the imposter is using "Microsoft Outlook Express 6.00.2600.0000". Consequently, it's very easy to tell that the email wasn't ours and that there is an imposter out there who is impersonating us.
Why would someone want to impersonate us? Well, for starters, although they might not be able to infect us with a virus because we are using virus software and are immune, they might try indirectly to make trouble for us. For instance, they might send us bogus emails like that above to convince us that we have a virus so that we will want to:
-
Slick our computer and completely reinstall everything to get rid of the problem.
-
Buy virus software and install it. Sometimes, they will even send an email to your computer offering a virus program for a massive discount that is actually snoopware that they can use to steal information off your computer and monitor your operations! Don't buy virus software through the internet or email! Always purchase locally from a trusted source.
-
Spend money on a computer professional to diagnose whether we have a problem, which we obviously don't.
The above can be a very effective approach to make trouble against people who are computer illiterate. If you have read this article and understand it though, then the dishonest techniques listed above don't work against you! How do we catch these imposters and get them in trouble? If you wanted to find out whose IP address this was, you would go to SamSpade.org and look up the owner:
Type in the above IP address "66.134.52.82" on the line with the button next to it that says "IPWhoIs" and then click on the button. Below is what you get:
Trying whois -h whois.arin.net 66.134.52.82
Error - couldn't connect to server
Trying whois -h whois.arin.net 66.134.52.82
OrgName: Covad Communications
OrgID: CVAD
Address: 2510 Zanker Rd
City: San Jose
StateProv: CA
PostalCode: 95131-1127
Country: US
ReferralServer: rwhois://rwhois.laserlink.net:4321/
NetRange: 66.134.0.0 - 66.134.255.255
CIDR: 66.134.0.0/16
NetName: COVAD-IP-2-NET
NetHandle: NET-66-134-0-0-1
Parent: NET-66-0-0-0-0
NetType: Direct Allocation
NameServer: NS1.COVAD.NET
NameServer: NS2.COVAD.NET
Comment: ADDRESSES WITHIN THIS BLOCK ARE NON-PORTABLE
Comment:
Comment: for abuse issues, please contact abuse-isp@covad.com
Comment: Reassignment information for this block
of addresses can be found at rwhois://rwhois.laserlink.net:4321/
RegDate: 2001-07-13
Updated: 2003-05-13
TechHandle: ZC178-ARIN
TechName: Covad IP Admin
TechPhone: +1-408-434-2108
TechEmail: ip_admin@covad.com
AbuseHandle: CART-ARIN
AbuseName: Covad abuse reporting team
AbusePhone: +1-703-376-2830
AbuseEmail: abuse-isp@covad.com
OrgAbuseHandle: CART-ARIN
OrgAbuseName: Covad abuse reporting team
OrgAbusePhone: +1-703-376-2830
OrgAbuseEmail: abuse-isp@covad.com
OrgNOCHandle: CIN-ARIN
OrgNOCName: COVAD IP NOC
OrgNOCPhone: +1-888-801-6285
OrgNOCEmail: noc-ipservices@covad.com
OrgTechHandle: PRN-ARIN
OrgTechName: Nicoll, Peter R
OrgTechPhone: +1-408-434-2108
OrgTechEmail: pnicoll@covad.com
# ARIN WHOIS database, last updated 2003-08-27 19:15
# Enter ? for additional hints on searching ARIN's WHOIS database.
This is very useful information, because now we have someone to complain to! We can write the abuse email address above, at "abuse-isp@covad.com" and tell them that the IP address of "66.134.52.82" is spoofing or impersonating our email address and ask them to terminate the account of the offender and tell us who it is so we can prosecute them. Make sure you include the original email you received back so they can use that information to trace the offender down and nail him. Here was that email:
This message was created automatically by mail delivery software.
Message violates a policy rule set up by the domain administrator
Delivery failed for the following recipients(s):
ewhr@edwards.com
----- Original Message Header -----
Received: by mail6-kan (MessageSwitch) id 1062107549539335_11622; Thu, 28 Aug 2003 21:52:29 +0000 (UCT)
Received: from LIZAVETA (h-66-134-52-82.LSANCA54.covad.net [66.134.52.82])
by mail6-kan.bigfish.com (Postfix) with ESMTP id C9257174762
for <ewhr@edwards.com>; Thu, 28 Aug 2003 21:52:03 +0000 (UCT)
From: <johnhamilton@aol.com>
To: <ewhr@edwards.com>
Subject: Re: Wicked screensaver
Date: Thu, 28 Aug 2003 14:50:29 --0700
X-MailScanner: Found to be clean
Importance: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MSMail-Priority: Normal
X-Priority: 3 (Normal)
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="_NextPart_000_00467D97"
Message-Id: <20030828215203.C9257174762@mail6-kan.bigfish.com>
Now we are getting somewhere!